Cybersecurity breaches are a growing concern for businesses worldwide. Whether they result from malevolent external attacks, malicious and disgruntled employees, or employees falling for scams, the financial impacts and other reputational damage can be significant. After examining several important reasons why cybersecurity is crucial in today’s world, this blog shortlists the top cybersecurity crowdsourcing platforms.
Catch up on latest thoughts and trends in crowdsourcing cybersecurity in our Crowd // Sessions webinar on January 30th, 2025, “Unlocking the Power of Crowdsourced Cybersecurity.” Free registration is open now to guarantee your place. You’ll learn about rapid identification of vulnerabilities; being proactively defensive, and compliance and regulation.
Why Cybersecurity is Important
Breaches can be Very Expensive
According to the IBM Security and Ponemon Institute’s “Cost of a Data Breach Report 2023”, the global average cost of a data breach reached a staggering $4.45 million. This represents a 15% increase over the past 3 years. Researcher Cybersecurity Ventures predicts the global annual cost of cybercrime will reach a staggering $10.5 trillion USD by 2025. This emphasizes the immense financial burden cybercrime places on businesses globally. It’s important to remember that these figures only reflect the financial cost. Breaches can also damage a company’s reputation, lead to lost customers, and negatively impact employee morale.
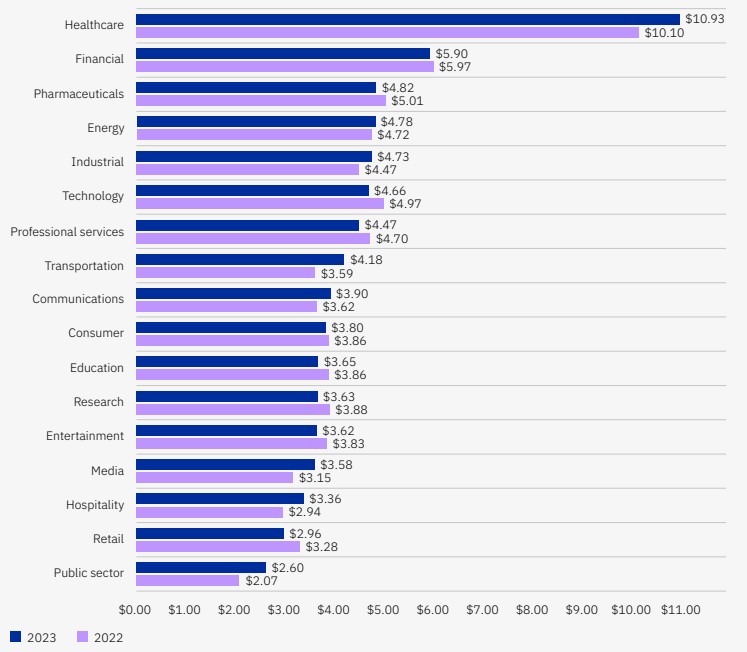
The Costs of a Data Breach by Industry Sector
(in US$ millions)
Data Protection
Our increasing reliance on technology means vast amounts of sensitive data are stored online, from financial records to personal information. Strong cybersecurity safeguards this data from unauthorized access, theft, or damage by cybercriminals.
Prevention of Disruptions
Cyberattacks can disrupt critical systems and services, causing financial losses and operational slowdowns. Effective cybersecurity measures minimize these risks and ensure smooth functioning of essential systems.
Maintaining Trust
Data breaches and cyberattacks erode trust in organizations. Robust cybersecurity demonstrates a commitment to protecting user data and fosters confidence in your services.
Compliance with Regulations
Many regulations require organizations to implement cybersecurity measures to protect user data. Strong cybersecurity practices ensure compliance and avoid legal repercussions.
Safeguarding Critical Infrastructure
As our infrastructure becomes more reliant on technology (power grids, transportation systems, other smart city technology), cyberattacks pose a serious and growing threat. Cybersecurity is essential to protecting these critical systems and ensuring public safety and trust in governance.
Overall, cybersecurity is therefore an essential practice for individuals and organizations alike. It protects our valuable data, ensures smooth functioning of essential systems, and fosters trust in the digital world.
Benefits of Crowdsourcing Cybersecurity
The commonly cited benefits of using a cybersecurity crowdsourcing platform include the following:
Access to an On-Demand Talent Pool
Crowdsourcing leverages a global pool of cybersecurity experts, which can provide diverse skills and perspectives not available in-house. These people are often already accomplished security testers and providers, and their key motivation is to accelerate gaining wider experience. Critically, research by one of the major crowdsourced cybersecurity platforms shows the increased incidence of security breaches is outpacing the growth in the number of specialists who can deal with it. Access to an on-demand workforce is thus vital to maintain secure defenses and handle any breaches.
Cost-Effectiveness
Crowdsourcing on-demand “white-hat” hackers invariably reduces costs associated with hiring full-time cybersecurity professionals. Companies can pay for specific tasks or results rather than maintaining a large, in-house team.
Speed and Efficiency
Crowdsourcing can expedite the identification and resolution of security vulnerabilities, as multiple experts work simultaneously on the same problems. Using a global network of ethical hackers means issues are worked on 24/7.
Continuous Monitoring
A crowdsourced approach ensures ongoing scrutiny of systems, as opposed to periodic checks, leading to more proactive and continuous security measures.
Enhanced Creativity and Innovation
External experts can bring innovative solutions and unconventional thinking to cybersecurity challenges, which may not be possible with a standard team.
Scalability
Crowdsourcing provides the flexibility to scale cybersecurity efforts up or down based on the current needs without long-term commitments.
Real-World Testing
With diverse experts mimicking real-world attack strategies, companies can get a more accurate assessment of their security posture and vulnerabilities.
Top 3 Crowdsourced Cybersecurity Platforms
There appears to be wide acceptance that the top three cybersecurity crowdsourcing platforms are HackerOne, Bugcrowd and Synack. All three provide a comprehensive range of services, and have access to large global networks of ethical hackers.
HackerOne is one of the largest and most popular bug bounty platforms, and it also offers vulnerability disclosure programs and penetration testing services. It believes its combination of human insight provided by its network of over one million hackers, coupled with AI precision, delivers unbeatable security.
The use of AI is vital, because malevolent hackers are harnessing its power to speed up and escalate their enterprise attacks.
HackerOne’s Leaderboard gamifies competitiveness between its hackers and enhances personal reputations. The platform is used by leading organizations including Google, Microsoft, and the U.S. Department of Defense.
Bugcrowd was founded in 2012 and is headquartered in San Francisco, California. It provides a comprehensive range of services including penetration testing, bug bounties and vulnerability disclosure. The researchers, aka ethical hackers, can choose to work on any projects posted on Bugcrowd, and compete with others for the financial rewards that are available. This built-in competitiveness gives customers quick turnaround times to test their sites and apps for vulnerabilities. The most competent researchers may then be invited to work on private projects with potentially higher rewards and less competition – though what competition there is will be tough!
The Bugcrowd Leaderboard is updated at the beginning of every month. Each researcher’s ranking on the leaderboard is based on their total number of kudos points earned over all-time and over the previous month.
Bugcrowd connects organizations with its global community of security researchers, who are paid via PayPal and Payoneer. PayPal is available in more than 200 countries/regions, and whilst it supports 25 currencies many of Bugcrowd’s network may thus require currency exchanges to use their income.
The platform is used by major companies such as Tesla, Mastercard, and Fitbit.
Synack, which is based in California and was founded in 2013, also provides a comprehensive range of cybersecurity services, harnessing a vetted community of some of the world’s most talented security researchers to deliver continuous penetration testing and vulnerability management. It combines crowdsourced cybersecurity with advanced AI technology to provide high-level security testing.
Customers that build and augment their security testing capabilities and capacity by working with Synack include DARPA (Defense Advanced Research Projects Agency – the research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military), and several Fortune 500 companies.
Other Cybersecurity Crowdsourcing Platforms
These cybersecurity crowdsourcing platforms tend to focus on particular types of threats, rather than on the full range. As to which platforms would be considered among the best for any potential customer user thus depends on their specific circumstances and requirements. These platforms are certainly more than worthy of consideration, and offer unique advantages by harnessing the collective power of cybersecurity experts worldwide, providing companies with a robust and dynamic approach to securing their digital assets.
Cobalt was founded in 2013 and is headquartered in San Francisco, California. It focuses on providing Pentesting as a Service (PtaaS). It uses a curated community of testers and provides detailed reporting and remediation guidance. It is used by companies like HubSpot, GoDaddy, and Vonage.
YesWeHack is a European-based platform for bug bounty and vulnerability disclosure programs, and is headquartered in Paris, France. It was founded in 2015 to provide a secure environment for companies to interact with its current network of tens of thousands of ethical hackers who uncover vulnerabilities in websites, mobile apps, connected devices and digital infrastructure. Clients include Orange, Qwant, Swiss Post, Bla Bla Car and the French government.
Bishop Fox is recognized as a leading authority in offensive security, providing solutions ranging from continuous penetration testing, red teaming, and attack surface management to product, cloud, and application security assessments. Offensive security is a “forward defense” approach that proactively uncovers and eliminates exposures before they are exploited. Bishop Fox is based in the US state of Arizona, and was founded in 2005. It works with clients from various industries, including finance, healthcare, and technology.
Intigriti is a European platform based in Antwerp, Belgium. It is well known for its focus on quality and providing a curated pool of vetted security researchers. Its community of ethical hackers challenge their customers’ security against realistic threats in precisely the same way malicious hackers do. Intigriti goes beyond traditional pentesting or bug bounty programs, and its customers publicly acknowledge Intigriti’s advanced guidance and unmatched agility. The platform provides real-time reports of current vulnerabilities and commonly identifies crucial vulnerabilities within 48 hours. It was founded in 2016, and its clients include Coca-Cola, Nestle, Microsoft and Revolut.
“The BOLD Awards’ Gala Dinner 2025 will bring together the world’s leading innovators for an exclusive night of networking, learning, recognition and entertainment. Non-finalists in the 33 categories of digital industries (which includes Cybersecurity) and the technology that powers them are very welcome to request a VIP Invitation to attend. There is also still time to enter BOLD Awards before the deadline of December 6th, 2024. The future belongs to the BOLD. See you all in Lisbon on March 28th, 2025.”
Epi Ludvik, Crowdsourcing Week and BOLD Awards CEO

Don’t forget our webinar on January 30th, 2025. Free registration is open now to guarantee your place.




0 Comments