In any difficult times, fraudsters and malefactors always step up their activities, which can lead to disastrous consequences for any business. The massive and hasty transition of companies to remote work has led to an increase in the number of successful cyberattacks. Moreover, they are becoming more sophisticated – new methods of fraud, improved viruses, and Trojans aimed at stealing confidential data appear every day. Unfortunately, it is confirmed by sad statistics proving that in the first half of 2020, the level of intrusion incidents was 154% higher than in 2019. Cybersecurity for freelancers is a growing risk, though there are some simple precautions to take.
Home networks are much less protected than corporate networks, putting any remote employee, freelancer or gig-economy worker at a cybersecurity risk. Risks associated with remote work include traffic modification, interception of passwords and confidential data, as well as hacking of routers and redirecting users to malicious sites. Any computer connected to a corporate network can get infected.
The first symptoms of cyber-coronavirus are the appearance of suspicious files and applications on the device and poor system performance for no reason. We’ll take a look at which information security solutions have become the most relevant for both companies organizing remote work and freelancers taking projects, like dissertation help and web design, from job platforms.
To begin, though, let’s remind ourselves of the basic safeguards to increase cybersecurity for freelancers, and other remote workers.
Standard Safety Policies
Every person who is using a worldwide net for remote work should follow the simplest rules that always work to maintain cybersecurity for freelancers:
- Check your home router settings. If you work from home, all the traffic will go via your home router. Criminals can hack it, get access to Wi-Fi traffic and the whole network. To prevent this from happening, you need to check the settings.
- Make sure there are no unwanted devices connected to your home network. You may use scanners to find all the devices on your home network. It will allow the timely detection of an intruder. If you spot an unfamiliar device, delete it and change the Wi-Fi password.
- Upgrade the router’s firmware. It should be updated to the latest version.
- Do not open emails with attachments. The best approach is to use antivirus with the Anti Phishing module and the email filtering function.

Photo by Etienne Boulanger on Unsplash
These components should be present in the arsenal of any company that takes care of their information security. Remote work is no longer exotic and, therefore, protection of remote connections must be included in the main list of information security policies. It is crucial to remember about prevention and observe basic rules of digital hygiene. Being careful when dealing with virtual threats is just as important as washing your hands, treating surfaces with an antiseptic, or wearing a mask during the pandemic.
To take cybersecurity for freelancers and other remote workers further, we have considered secure VPN connection, multi factor authentication, data-leakage protection (DLP), and control of privileged users (PIM / PAM).
VPN Connection
The first and foremost task is to protect the communication channels used for information exchange. You may solve it with the help of software and hardware VPN (virtual private network) products. If your work requires you to connect to public or unfamiliar networks while abroad, consider using a VPN for travel to ensure your sensitive data remains protected even in high-risk locations.
Thanks to VPN, you can access your work information from anywhere in the world, because this is the connection between you and the server located in your office. The tunnel goes through many server providers, there may be many points through which data passes. But the encryption itself is established between the client and the server. If someone tries to connect as Man-In-The-Middle, the session will be terminated. Yes, data passes through many providers, but it is almost impossible to decrypt this traffic if you have configured VPN service correctly.
There are Open Source solutions that are well-suited for individual entrepreneurs, and there are commercial solutions for bigger companies when ready-made hardware is installed and supplied to some clients.
Multi-Factor Authentication
Strong authentication, or cryptographic authentication, is the process of authentication of an information system entity, implemented using cryptographic algorithms and protocols.
The main idea of strong authentication is that the authenticated party, in the process of exchanging messages with the authentication server, sends it some messages that are protected from forgery by attackers using cryptographic transformations.
There are several types of authentication:
- one-factor or simple authentication implies using a password;
- two-factor authentication. The first factor is the knowledge of the system user name and password as a rule. The second factor is a one-time password or electronic signature generated using an electronic medium that stores the private key of the authenticated subject. Sometimes, you can use a PIN-code as an additional element of the second factor of authentication. It enables usage of a hardware module with a private key to authenticate messages during an exchange;
- multi-factor authentication adds some biometric characteristics of the user to the above two authentication factors. It can be a fingerprint, a voice recording, a face photograph, a drawing of the retina or iris, keyboard handwriting when entering a password, etc.
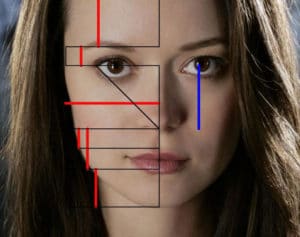
Facial geometry recognition is being used more often as a means of cybersecurity for freelancers and other remote workers
Systems with biometrical authenticating elements are not yet very widespread. Though there are already solutions on the market (such as LastPass, RSA SecurID® Access and Secret Double Octopus) that allow user authentication by two devices interacting via Bluetooth, or by voice and face geometry. The use of multifactor authentication systems of this type looks quite promising.
Data-leakage Protection
Dedicated software solutions prevent the loss of confidential information. They are based on the analysis of data flows crossing the perimeter of the protected information system. “When confidential information is detected, an active component of the system is triggered, and the transmission of a message (packet, stream, session) is blocked or a copy of the traffic is saved for post-analysis in case an investigation of a possible leak is conducted,” says an Online Security Specialist from Ivory Research.
 Implementation and support of DLP require a fairly large investment and effort on the part of the company. However, look on it as insurance: this measure can significantly reduce the level of information risks for a company’s IT infrastructure. By introducing monitoring complexes with a DLP component, a business will not only reliably protect data, but will also be able to keep track of working hours, separating the productive activity of staff from the malicious. The program allows analyzing productivity in a matter of minutes. The monitoring mode can be turned off by the employees, thus minimizing any potential moral discomfort.
Implementation and support of DLP require a fairly large investment and effort on the part of the company. However, look on it as insurance: this measure can significantly reduce the level of information risks for a company’s IT infrastructure. By introducing monitoring complexes with a DLP component, a business will not only reliably protect data, but will also be able to keep track of working hours, separating the productive activity of staff from the malicious. The program allows analyzing productivity in a matter of minutes. The monitoring mode can be turned off by the employees, thus minimizing any potential moral discomfort.
PIM/PAM Technologies
This class of solutions (Privileged Identity Management or Privileged Access Management) is designed to make it difficult to penetrate the network and gain access to privileged accounts, as well as to strengthen the protection of privileged user groups. PAM also enhances monitoring, visibility, and granular control over privileged accounts.
The essence of such systems boils down to the fact that privileged users’ sessions are recorded. They provide the possibility of viewing and convenient search for information on them in order to prevent dangerous actions of users. If necessary, passwords can be changed after any session.
Our CSW Crowd Session covering Crowdsourcing Cybersecurity takes place January 28 2021. It provides a 90 minute window to learn about the opportunities and possibilities with crowdsourced cybersecurity and why you should care about it NOW more than ever. Further details and tickets are available.




0 Comments